Cybersecurity Basics for Businesses

Businesses increasingly rely on technology to store and manage sensitive information. In addition, hackers and cybercriminals are constantly evolving their tactics. As a result, businesses need to be vigilant about their cybersecurity practices to stay protected.
Because the threats are everywhere.
Common Cyber Threats
What threats to your data will you encounter most frequently?
- Ransomware: Malware designed to lock away data the victim pays a ransom to release it
- Malware: Malicious software
- Phishing: Messages or websites that mimic legitimate sources and trick people into revealing confidential information
- Social Engineering: Mining social media accounts for information that may be used to access financial or other sensitive data
- Distributed Denial-of-Services Attacks: DDoS attacks attempt to overload a system with traffic
- Man-in-the-Middle Attacks: So-called “eavesdropping” attacks that intercept unprotected messages between two individuals or systems
- Insider Threats
- Brute Force
According to Statista, phishing is the most common type of cybercrime worldwide. It occurs 5x more frequently than the second most common, personal data breach. And while phishing attacks happen in every industry, the top three most targeted in 2022 were financial (23.6%), SaaS/webmail (20.5%), and retail/e-commerce (14.6%).
Cybercrime by the Numbers
The data paints a rather bleak picture.
- Cybersecurity spending is expected to top $188 billion in 2023
- The global average cost of a data breach in 2022 was $4.35 million, while the American average was more than twice as high at $9.44 million
- Online fraud will cost the e-commerce industry $25 billion each year by 2024
- More than 550,000 new pieces of malware are identified each day
- A malware attack costs an average of 50 lost days for a business
- While small businesses account for 43% of all cyberattacks, only 50% of SMBs have a cybersecurity plan
- Security Magazine estimates that there are 2,200 cyberattacks each day, or 1 every 39 seconds
- 50% of American internet users experienced a data breach in 2021
- As much as 95% of all data breaches are the direct result of human error
The takeaway? Cybercrime is prevalent, on the rise, costly, and typically the result of human mistakes. The good news is that human mistakes can be identified and fixed. As a business owner starting from scratch, here’s how to use cybersecurity to protect your business.
Basic Cybersecurity Tactics
So what can a business owner do to mitigate the risks? That’s a complicated answer that depends on your size, industry, and workflows. But every business should be doing something. Think you’re too small to be attacked? Believe you’re safe because you’re not a “digital company”? Think again.
Strong Passwords and Multi-Factor Authentication
Passwords are your first line of defense against unauthorized access to sensitive data. It’s important to use strong passwords that aren’t easy to guess, as well as different passwords for different accounts. (Never reuse a password.)
Don’t use obvious or easy-to-find information like birthdays or names. Check out the list of worst passwords that come out every year for a quick reference on which ones to avoid at all costs. Several of them—including password, 123456, qwerty, and 111111—appear year after year. These are only too easy for a hacker to guess.
Another important factor to consider is password length. The longer the password, the more difficult it is to crack. A good rule is to use passwords that are at least 10 characters long. The longer, the better. A 14-character password using letters, numbers, and symbols, for example, would take a million years to hack.

A strong password, then, is a unique combination of 10+ uppercase letters, numbers, lowercase numbers, and symbols.
Implement a policy that employees must use a password manager like Dashlane or Bitwarden. These solutions remember passwords and use a built-in generator to create strong passwords instantly.
You can also implement multi-factor authentication (MFA) on important platforms. This requires a user to provide two or more identifiers to log in. For example, an account with MFA enabled might require a password and a fingerprint scan, a PIN sent to your device, or a passcode from an authenticator like Authy. Unauthorized users can’t gain access even if they have the password.
Offsite Servers
Many businesses use on-premise servers to store their data. However, those are vulnerable to physical threats such as natural disasters or theft. In addition, it takes time and money to keep them in peak working order. And unless you have a dedicated IT specialist keeping an eye on them, they may be hacked without you even knowing.
The solution? Offsite—aka cloud—servers.
Cloud storage can provide a higher level of protection because they’re managed by third-party providers who specialize in digital security. These providers have the resources and budget that you may lack, and their only task is keeping your data safe. They’ll do whatever it takes because anything less than stellar impacts their reputation and bottom line.
As a bonus, you can access offsite servers from anywhere, making it easier to share data and collaborate with remote employees. And they’re often more scalable than on-premise servers, allowing businesses to add or remove resources as necessary.
Popular providers include heavyweights like Amazon and Google. No matter what, go with a reputable cloud provider with a rock-solid track record. Look for providers that use encryption to protect data in transit and at rest, regular backups, and multiple layers of cyberattack security.
And don’t forget to read the provider’s service level agreement. This outlines their responsibilities and guarantees regarding uptime and data protection.
Cybersecurity Training for Staff
If most cyberattacks are the result of human error, you need to train your staff on how to avoid them.
Employees are often the weakest link in a business’s cybersecurity plan because they may not be aware of threats or understand the importance of cybersecurity protocols. Providing training can help prevent cyberattacks and improve the overall security of your business.
This training should include password security, common phishing scams, how to recognize suspicious activity, and more. It’s important to make cybersecurity training a regular part of employee onboarding and to provide ongoing training to ensure that employees stay up-to-date with the latest threats and best practices.
Phishing scams—where cyber criminals attempt to trick individuals into providing sensitive information—are a common way that attackers gain access to business networks. It may look legitimate, but there are usually clues. Teach your staff about red flags like phony email addresses and URLs, spelling and grammar mistakes, or a missing SSL certificate.
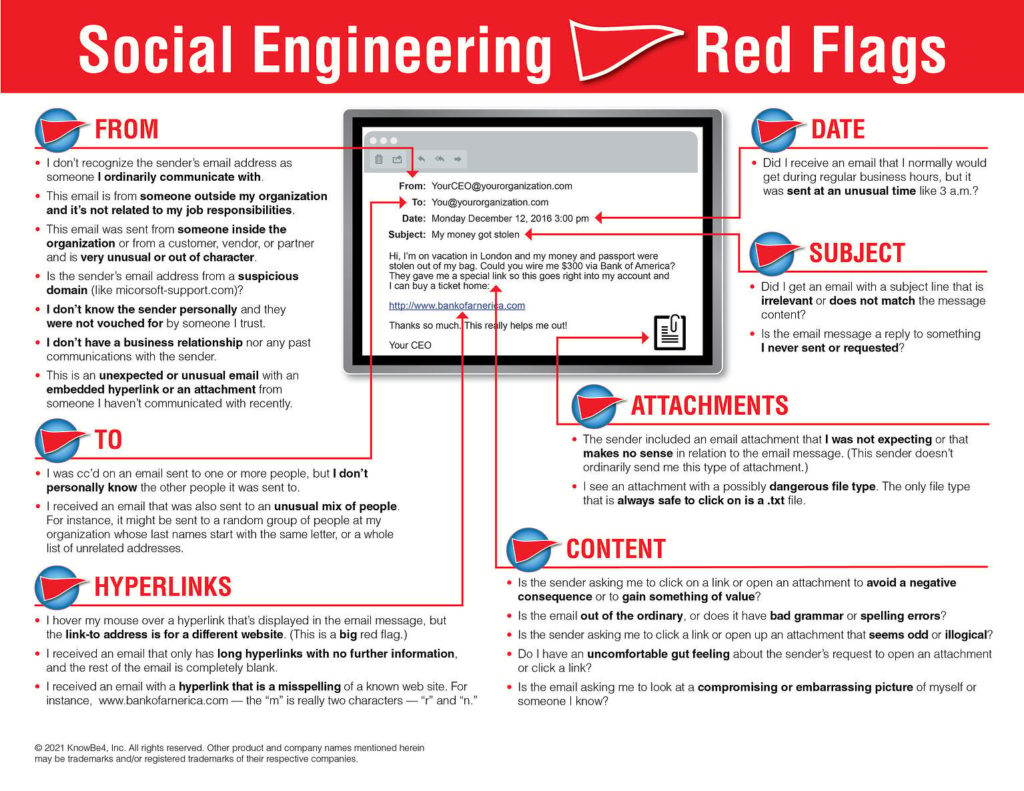
Source: www.phishing.org/what-is-phishing
Good cybersecurity training empowers employees to trust their gut. If something feels “off,” it often is. When in doubt, avoid clicking on links and downloading attachments. Confirm any suspicious requests with the sender directly through a different communication channel.
But it doesn’t end there. Employees should be trained on how to handle sensitive information like customer data or financial records. Best practices include keeping passwords and log-in credentials private, locking their computers when they step away, and securely disposing of physical documents as mandated by company policy.
No training program in the modern age is complete without cybersecurity training, too.
Data Backups
Remember the advice to avoid putting all of your eggs in one basket? It applies to digital data, too.
Regular backups are an essential part of any cybersecurity strategy. In the event of a cyberattack, backups can help businesses recover their data and minimize the impact of the attack. A ransomware incident can be devastating… unless you have the data available on other platforms and channels. Frequently backing up files can also help prevent data loss due to hardware failures, natural disasters, theft, or other unforeseen circumstances. It’s good for cybersecurity and business continuity.
You can store files with a generic cloud provider like Dropbox or Google Drive, or with a dedicated backup service like Backblaze or Crashplan. Regardless of which solution you use, you should store backups securely offsite, preferably in a different location than the primary data. This way, if the primary data is compromised in any way, the backups will still be available.
And don’t forget to test backups regularly to make sure that they’re working properly and that you can restore them in the event of a disaster.
Update Software and Hardware
Technology providers identify vulnerabilities all the time. These providers will release an update or patch to address the issues, in addition to introducing new features and bug fixes. But if you don’t update, you’ll be left exposed. Cybercriminals can exploit these vulnerabilities to gain access to your business’s sensitive data.
Outdated software is more vulnerable to attacks, and outdated hardware may not be able to support the latest security features. To ensure the security of your business’s technology, it’s important to stay up-to-date with the latest updates and upgrades.
If it has an automatic update feature, enable it. And if not, check frequently and manually update as necessary.
Quick Bonus Cybersecurity Tips
We’ve just scratched the surface. There’s a lot more you could do.
- Network Segmentation: Use network segmentation to create layers of security and limit the damage that a breach could cause.
- Secure Wi-Fi: Require everyone to use secure Wi-Fi networks with strong passwords and encryption.
- VPN: Secure your connections with a virtual private network, available from providers like NordLayer, Perimeter 81, and ExpressVPN.
- Incident Response Plan: Develop and test an incident response plan to respond to security breaches quickly and effectively.
- Third-Party Security: Empower employees and managers to implement trustworthy third-party security services and tools to strengthen internal security measures.
- Ongoing Monitoring: Keep an eye on systems and networks to detect and respond to threats immediately. That which gets monitored gets managed.
Upgrade Your Physical Security
While much of the focus on cybersecurity is on digital threats, physical security is also an important consideration for businesses. Physical security refers to protecting tangible assets like buildings, equipment, and more from unauthorized access or damage. Physical security measures can also help prevent unauthorized access to sensitive data, such as login credentials or financial records.
How do you get strong physical security? With Deep Sentinel.
By combining business security camera systems with live video monitoring, Deep Sentinel protects your business before, during, and after a crime happens. No other solution prevents criminal activity with such speed and accuracy.
Strengthen your physical and cybersecurity protocols, and you’re prepared for virtually anything.
Need a Solution that Prevents Crime?
Deep Sentinel is the only security technology that delivers the experience of a personal guard on every customer’s home and business. Visit deepsentinel.com/business or call 833-983-6006

